Risk Assessment & Compliance Automation
-
Enhance Efficiency: Speeds up at least 10x the risk assessment process.
-
Streamlined Compliance: Transparent, consistent documentation and reporting of risks and controls.
App Compliance - Real API Workflow Testing & Scanning Solutions | SaaS or On-premise
webtica.net is part of Doctor A Security.
ISO27001 & Critical Infrastructure (Computer-system) Ordinance
Traditional compliance methods are costly, time-consuming, and resource-intensive
Complex documentation
Our solution - Auditor grade, customizable policies and guidelines, mapped to Code of Practice CI(CS)O & ISO27002:2022.
Resource Intensive, months of preparation
Our solution - Streamlined workflows significantly reduce compliance time with minimum compliance teams involvement.
On-going Compliance Burden
Our solution - Continuous monitoring, automated alerts, and simplified compliance workflow.
AI-Powered Security Risk Assessment Automation
-
Systematic use of threats, assets & existing controls to identify sources and to estimate the levels of risk;
-
and the process of comparing the estimated risk against given risk criteria to determine the significance of the risk.
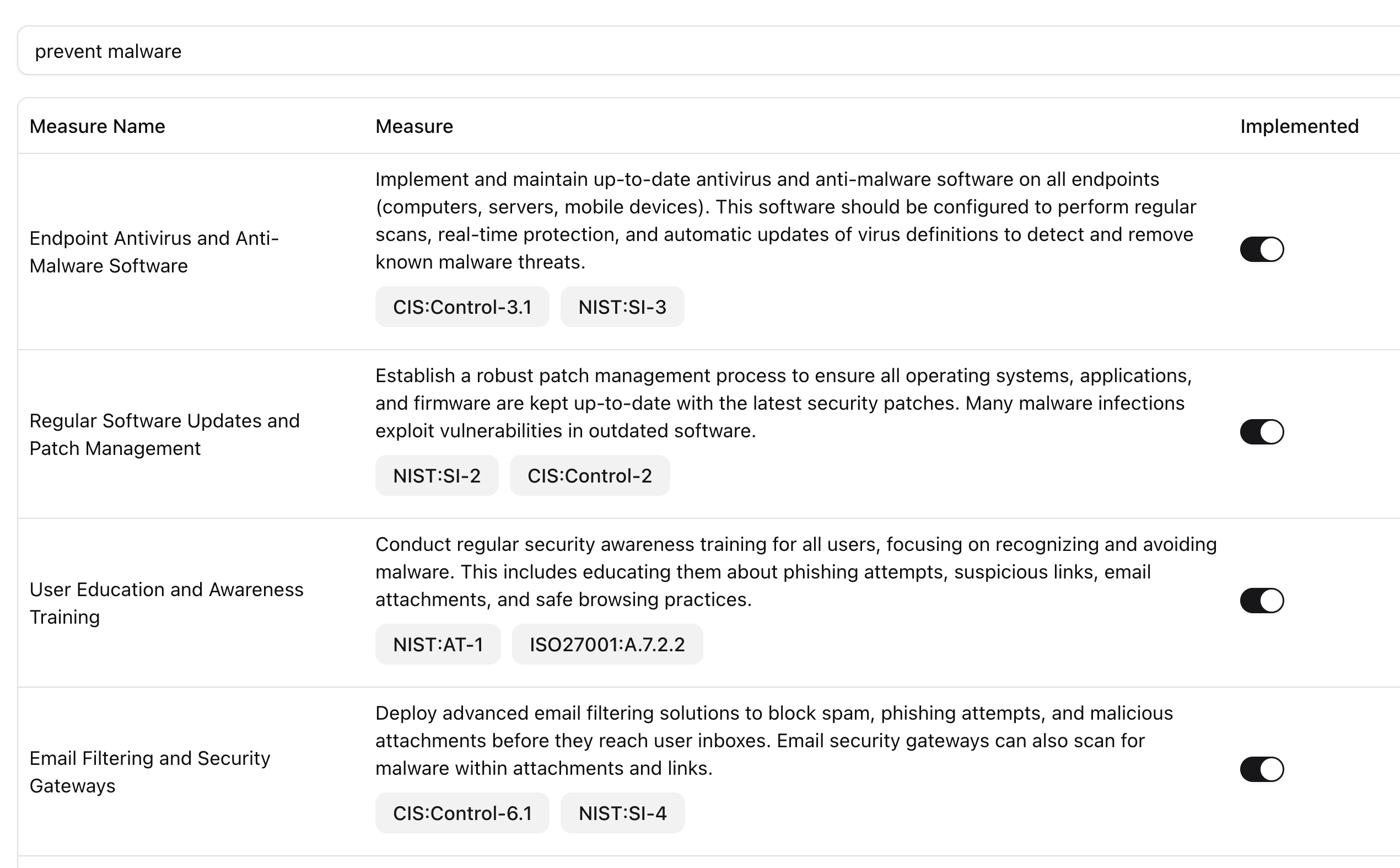
iAM Smart Workflow Testing, Mocking & Scanning

Multi-step Testing
Verifies that the end-to-end processes in an application function as designed, with security scan every step, ensuring a smooth and reliable user experience.

Code Review
Focuses on insufficient input validation involves a thorough examination of the code to identify where user input is not properly validated and sanitized.

QR Code Integration
Assess QR code usage across various processes, including authentication, "e-ME" Form Filling, and Digital Signing, and the processes for their creation and distribution.
Risk based IT Security Audit
Management Controls Review
How an organization manages and oversees the implementation and maintenance of security measures.
Operational Controls Review
The processes and procedures that organizations put in place to manage their systems and ensure they are securely operated.
Network Scanning
To identify active hosts, open ports, and other vital information. It helps assess network security, detect vulnerabilities.
Configuration Review
To ensure your IT systems, networks, and applications are configured to meet industry best practices and security standards.
Static Code Review
Focuses on insufficient input validation involves a thorough examination of the code to identify where user input is not properly validated and sanitized.
Validate Authorization
It builds upon successful authentication by confirming that the authenticated user or system has the necessary permissions or rights.
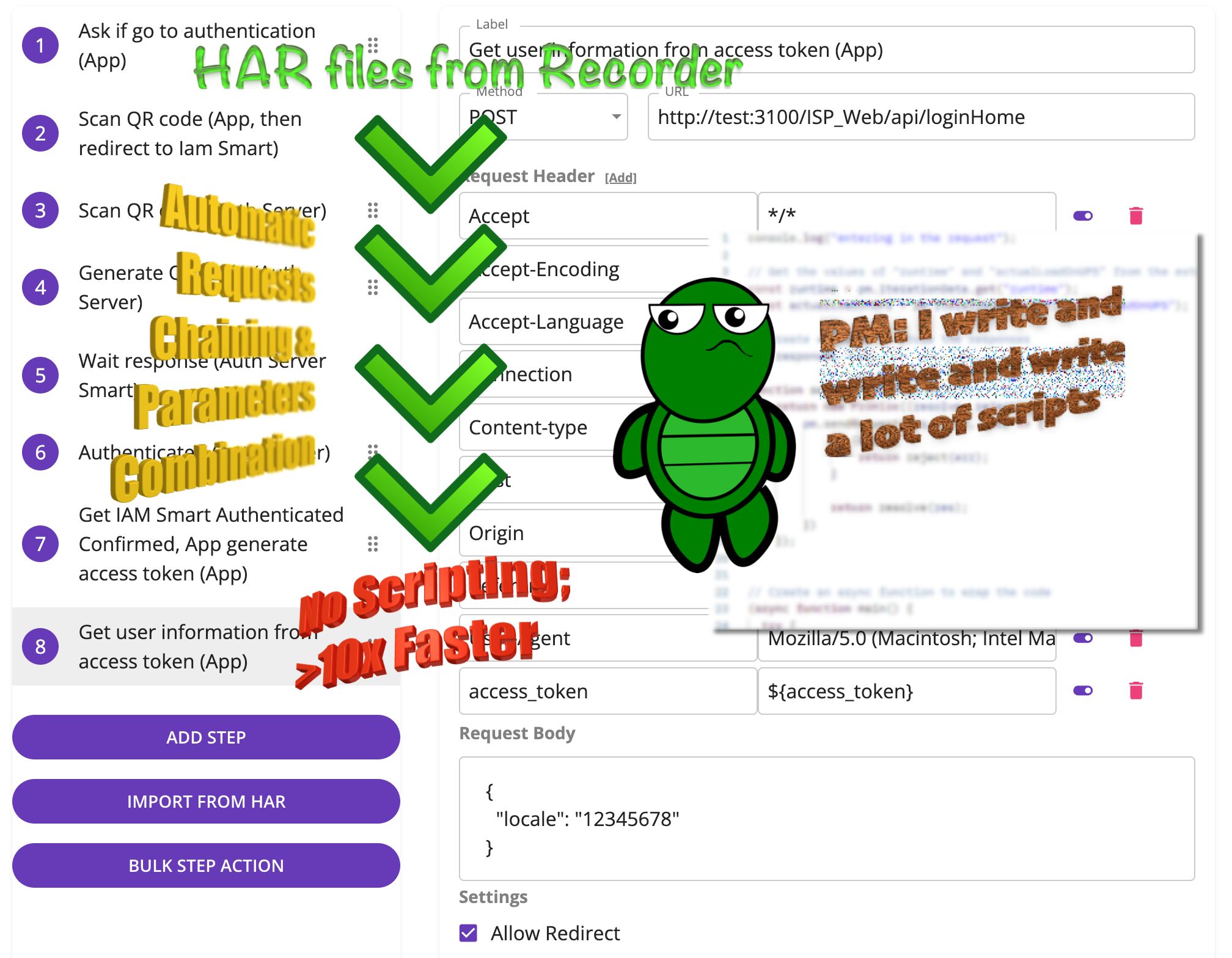
API Workflow Testing & Scanning
-
End-to-end testing covers complete application flows from start to finish. Each flow represents the sequence of actions a user will take in the application and can involve multiple endpoints and APIs.
-
API security scanning systematically tests APIs for vulnerabilities, misconfigurations, and other security flaws that could be exploited by attackers.
Risk based Privacy Impact Assessment
Data Processing Cycle Analysis
1) Purpose, 2) Retention, 3) Processing, 4) Security, 5) Policies & Practices & 6) Data Access & Correction.
Privacy Risk Analysis
1) List of Privacy Risks, 2) Functions & Activities of Data Users, 3) Nature of Personal Data involved, 4) Security, 5) Number of individuals affected, 6) Gravity of harm & 7) Controls effective to achieve acceptable risk levels?
Mitigating Privacy Risks
1) Necessary Collection, 2) Delete if no longer required, 3) Need-to-know access; 4) Appropriate Security Measures, 5) Easy to understand Privacy Policy, and 6) Consult Data Subject if significant Privacy Impact introducted.
PIA Reporting
When a project carries great public concern, the Data Users may see fit to have the PIA report published.

About Us
-
Established in the year 2000 in Hong Kong, by a team of IT security professionals.
-
Independent, not a reseller of any vendor.
-
We preach, we practice, we are certified in ISO/IEC 27001:2022 (and its predecessors) since 2003.
-
Specialized in Application Security Workflow Testing and Scanning.
-
Practicing Risk based IT Security Risk Assessment and IT Security Audit.
-
Develop Webtica.net, the Real API Workflow Testing and Scanning Solutions.
We’re Better. Here’s Why…

Independent
We are NOT a reseller of any vendor, free from bias and conflicts of interest, providing a more accurate and reliable services.

We Preach, We Practice
Actively implements and maintains a robust Information Security Management System (ISMS) based on the ISO 27001 standard.

Application Security Specialist
We focus on identifying and mitigating vulnerabilities in software applications to protect them from security threats.












